------------------------------------
Banner Grabbing with netcat
------------------------------------
So we're interested in knowing what's running behind port 80 and 21. We can use Netcat to grab port banners in the following way:
------------------------------------
Banner Grabbing with telnet
------------------------------------
Now that the hacker has a full list of services running on the target system, to be able to exploit them, he has to first figure out what software and version the service is. One way the hacker can get this information, is to telnet into service port. In the example below, we will use command prompt on Windows (Start -> Run -> Type “cmd” -> Enter). If you are on a Mac, you will be using the terminal. Note: If you are using Windows Vista, then telnet is not installed by default. You can install it by doing the following simple steps.
Banner Grabbing with netcat
------------------------------------
So we're interested in knowing what's running behind port 80 and 21. We can use Netcat to grab port banners in the following way:
So we know it's probably a Windows 2000 machine as it's running IIS 5.0 and Microsoft FTP Service.
Banner Grabbing with telnet
------------------------------------
Now that the hacker has a full list of services running on the target system, to be able to exploit them, he has to first figure out what software and version the service is. One way the hacker can get this information, is to telnet into service port. In the example below, we will use command prompt on Windows (Start -> Run -> Type “cmd” -> Enter). If you are on a Mac, you will be using the terminal. Note: If you are using Windows Vista, then telnet is not installed by default. You can install it by doing the following simple steps.
o Click Start then select Control Panel.
o Select Programs and Features.
o Select Turn Windows features on or off.
o Select the Telnet Client option and click OK.
o A box will appear to confirm installation. The telnet command should now be installed
o Select Programs and Features.
o Select Turn Windows features on or off.
o Select the Telnet Client option and click OK.
o A box will appear to confirm installation. The telnet command should now be installed
- First, the hacker would choose one of the open ports that were revealed in the Nmap scan to continue with and attempt to exploit. Let’s say that when the hacker scanned his target, he found the port 21 open. As you can see on the chart above, port 21 is FTP. To find out what FTP software is running he would use telnet by running the command:
telnet www.targetsite.com 21
- Next, it would connect to the target and display a banner telling the hacker the software and its version as shown below. This is the information the hacker needs to continue and begin searching for vulnerabilities for the software discovered.
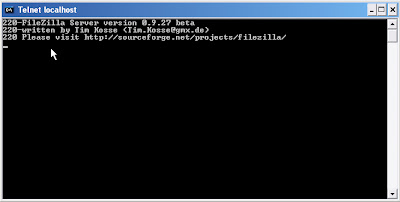
If the above method doesn’t work for you, then simply use Nmap’s full version detection option to get the information.



No comments:
Post a Comment
Note: only a member of this blog may post a comment.